As the new year approaches, we often make resolutions in our personal life – things we can do to make our lives better. Maybe it’s exercise, maybe it’s dry January or maybe you’re going to try to read a book a month. This year, I recommend that you make a resolution to improve the security where you work. The five items on this list will help you improve the security of your environment in less than five minutes each.
1. Review privileged groups
Studies have shown that most companies have far too many users in privileged groups. Over time, users may get assigned to admin roles and amass more and more admin privileges over time. If these admin accounts get compromised, they can cause extensive damage to the environment. It's a good idea to check how many users have administrative access, how many of them are Global Administrators, and if there are any invited guests or partners that have not been removed after being assigned to do an administrative task.
With Azure AD Access Reviews, you can manage users assigned to groups, enterprise applications and privileged roles to make sure users don't retain access for extended periods of time when they no longer need it. You can create an Access Review in less than five minutes. Just choose which role you want to be reviewed (Global Admin, Security Admin, etc.), select who will be doing the review of members and a start date and an email will be sent to the reviewer to approve or deny access.
Access reviews can also be used with external users, Microsoft 365 groups as well as Azure resource roles.
2. Turn on MFA for everyone
MFA is still the number one action you can take to prevent 98% of attacks on your accounts. In a recent article entitled Is MFA the Vegetable of Cybersecurity, I talked about how MFA adds another layer of protection to prevent threat actors from accessing your internal networks.
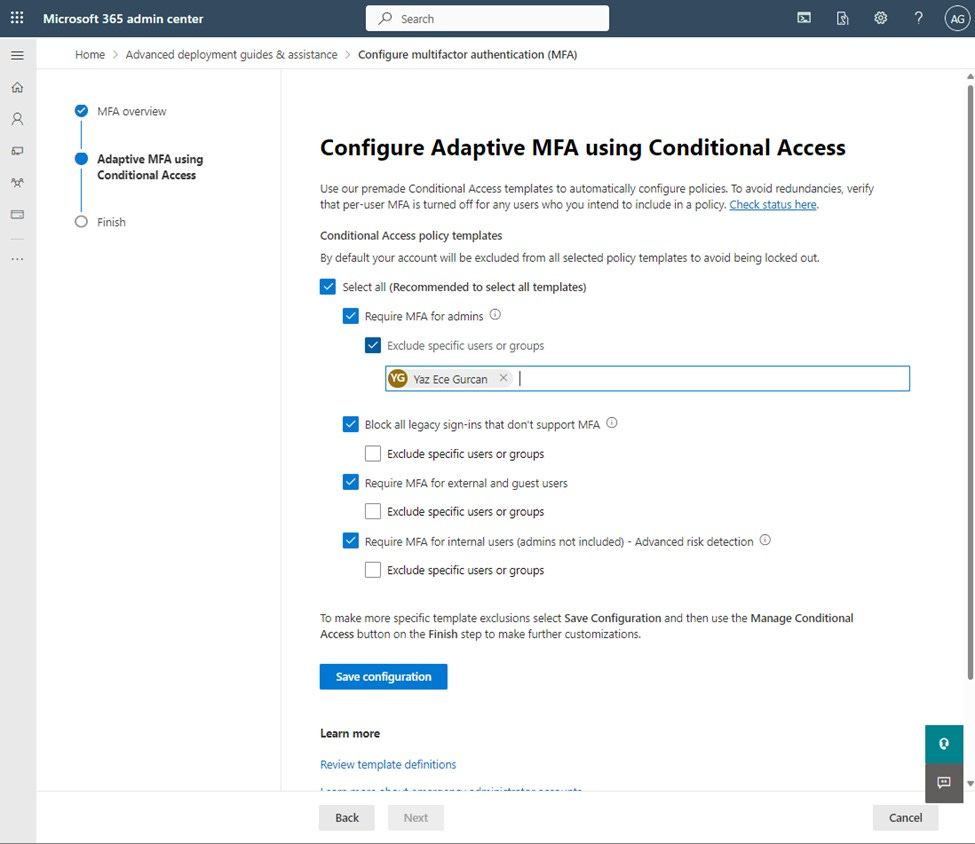
Now, we’ve made it even easier to adopt MFA using the new Zero Trust security model guidance that walks you through the steps to enable adaptive MFA with Conditional Access. You can simply click a check box and turn on policies that include “Require MFA for admins”, “Require MFA for external and guest users”, and “Require MFA for internal users”.
I’ve been surprised to see that many companies aren’t taking advantage of the cloud-protection feature in Defender antivirus. 96% of malware is seen once and never again so static virus definitions aren’t enough. We need machine learning. With the click of a check box, you enable our cloud protection which offers near-instant, automated protection against new and emerging threats. As a cloud service, it uses distributed resources and machine learning to deliver protection to all your endpoints at a rate far faster than traditional security intelligence updates – what we call “block at first sight”.
Within milliseconds of a client encountering a new file, multiple metadata-based machine learning models in the cloud started blocking these threats. Seconds later, our sample-based and detonation-based machine learning models go to work to verify the malicious classification. Within minutes, detonation-based models chime in and add additional confirmation.
Defender AV’s layered approach to security, which uses behavior-based detection algorithms, generics, and heuristics, as well as machine learning models in both the client and the cloud, provides real-time protection against new threats and outbreaks.
4. Enable user and domain impersonation protection
User and domain impersonation techniques have helped enable the rise of business email compromise (BEC) attacks. BEC attacks continue to proliferate showing up in 177 countries and causing losses of $26 billion since 2016. Both user and domain impersonation are forms of phishing where an attacker impersonates a sender address, display name or domain name to resemble a contact the user is familiar with to fool users into trusting them. For example, an address seems to be legitimate at first glance, but when you look more closely you see that an “m” is actually two “n”s, or a lowercase “L” is actually a capital “I”. Attackers count on the recipient’s previous relationship with the sender to gain their trust for a more authentic attack. This can cause the recipient to reveal confidential information, click on malicious links or even wire money to the sender.
You can easily enable Microsoft Defender for Office 365’s impersonation protection features in the anti-phishing policy. User impersonation protection can protect up to 350 internal users per policy in your organizations, as well as external users such as board members. When Microsoft detects an email with a sender that is impersonating a user, it will take whatever action you configure in the policy. The action could be to quarantine or delete the message or to redirect it to an admin mailbox.
Domain impersonation is also configured in the protection settings of an anti-phishing policy. You can specify a maximum of 50 custom domains in each anti-phishing policy. Each message is checked for impersonation if the message is sent to a recipient that the is in the policy and the appropriate action is applied.

 3. Turn on cloud protection
3. Turn on cloud protection


